The challenge
Health data - medical prescriptions, test results, notes explaining symptoms and sometimes very intimate patient information - is transmitted via a variety of digital tools. Exchanging and sharing data via these different digital channels exposes patient data to a number of very serious risks. Confidential data can be altered, its integrity impacted inadvertently or intentionally, stolen to be traded on illicit websites, or completely erased from the medium on which it is stored. These threats would be harmful to the patient if they were to occur. In some cases, these feared events could cause the patient's death.
Repositories and standards [HDH Regulation (Health Data Hosting)], good practices related to access to health data, applied and respected by organizations handling this sensitive information will significantly reduce these risks.
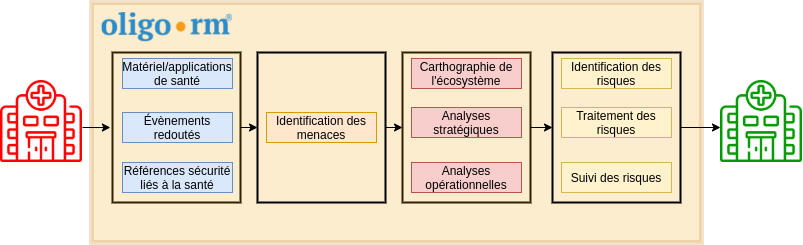
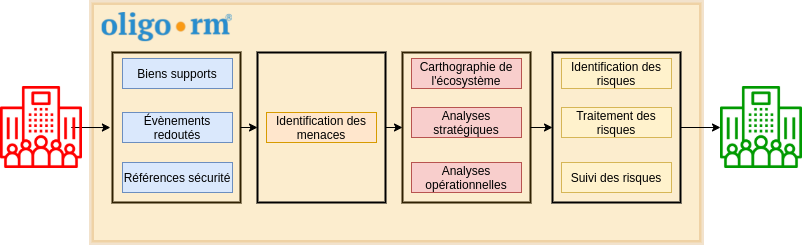
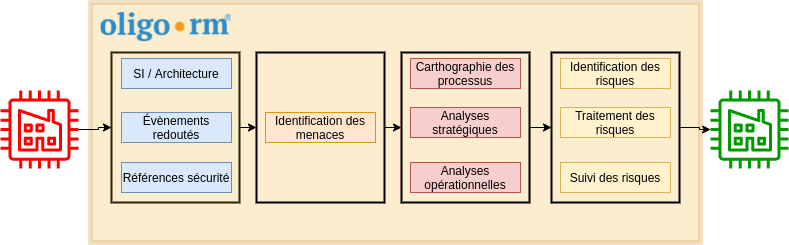
The OLIGO RISK MANAGER solution
Our OLIGO RISK MANAGER solution, a method for analysing and managing the risks associated with protecting health information and data, classifies this data according to its criticality and sensitivity, and identifies the threats that could impact its confidentiality, integrity and/or availability. It also involves assessing the level of threat that could come from the players handling this data, simulating risk scenarios linked to these threats to better counter them, putting in place a global security policy (access management, encryption, back-up, etc.), and finally, guaranteeing state-of-the-art compliance, meeting 100% of the standards in force.